Contents
- 1 Configuring Zoom with Shibboleth
- 1.1 Overview
- 1.2 Prerequisites
- 1.3 Configuring your Zoom Metadata in Shibboleth
- 1.4 Testing your Configuration
- 1.5 Frequently Asked Questions
- 1.6 Where is Zoom configuration?
- 1.7 How do I set up zoom on my computer?
- 1.8 How do I set up and set up a zoom meeting?
- 1.9 Why Bluetooth not working with Zoom?
- 1.10 Where is the Zoom sharing key?
- 1.11 How do I turn on Zoom sharing?
Configuring Zoom with Shibboleth
Overview
Zoom can be integrated with Shibboleth so that you can use your organization’s Shibboleth credentials for signing in to your Zoom account using Single Sign-On (SSO), which is supported by the Zoom API. Using SAML attributes, you can assign users Zoom licenses, add-on plans, roles and groups, as well as the features available in each.
Prerequisites
- Own a Zoom account or be an administrator.
- Accounts that are approved for business use and have a Vanity URL.
In the absence of an approved Associated Domain, the user will be sent an email via the account they have created that will ask them to confirm that they want to register for the account. Provisioning will take place automatically for any users that fall under a domain that is approved without requiring any email confirmation.
Configuring your SSO Information with Zoom
- Access the organization’s metadata and configure your SSO based on that information. Is usually located at https://IdP.DomainName/idp/shibboleth that can be accessed from any web browser.
- Navigate to the Single Sign-On page by logging in to your Zoom web portal.
- Fill in your SSO credentials from your metadata to make the page look like this:
- Sign up page URL: you can choose one of two binding options as shown after the Location= after the URL: POST Binding or Redirect Binding

- Sign-out page URL: This is optional. If you want to enter a Sign-out page URL, choose the corresponding POST or Redirect URL that appears in SingleLogoutService, after Location=.

- Identity Provider Certificate: Whenever you need to use a X509 certificate, you should use the first one that appears in your metadata.

- Service Provider (SP) Entity ID: Make sure you select the Service Provider (SP) Entity ID that includes https://, for instance, https://yourVanityURL.zoom.us
- Issuer (IDP Entity ID): For the full Entity ID, you will need to enter it as mentioned in the IdP metadata, for example: https://IdP.yourorganization/idp/shibboleth

- Binding: You have the option to choose either a POST or Redirect binding based on the URL of the sign in page.
- Unless you have disabled Shibboleth’s support for encrypted assertions, be sure to check Support Encrypted Assertions.

Note: In order to use CAS with Shibboleth, it should be used with HTTP-Redirect to bind the authentication.
- Sign up page URL: you can choose one of two binding options as shown after the Location= after the URL: POST Binding or Redirect Binding
Configuring your Zoom Metadata in Shibboleth
- The Zoom metadata can be downloaded from this site: https://yourVanityURL.zoom.us/saml/metadata/sp
- Adding a metadata element to the relying-party.xml file, which specifies the Zoom metadata as trusted by Shibboleth, will configure the Zoom metadata as trusted.
Example:
<MetadataProvider id=”Zoom_SP_Metadata” xsi:type=”ResourceBackedMetadataProvider”
xmlns=”urn:mace:shibboleth:2.0:metadata”>
<MetadataResource xsi:type=”resource:FilesystemResource”
file=”/var/shibboleth-idp/metadata/zoom_sp_metadata.xml” />
</MetadataProvider> - Your IdP should configure the SAML attribute of your email address at the very least.
Attribute Common SAML Attribute Name Email Address* urn:oid:0.9.2342.19200300.100.1.3 First Name urn:oid:2.5.4.42 Last Name urn:oid:2.5.4.4 The following SAML Attribute Name can be used for eduPersonPrincipalName if it is formatted as an email address: urn:oid:1.3.6.1.4.1.5923.1.1.1.6
You can do this by adding a new element under the AttributeFilterPolicy section of the attribute-filter.xml file.
Example:
<AttributeFilterPolicy id=”releaseToZoom”>
<PolicyRequirementRule xsi:type=”basic:AttributeRequesterString” value=”yourVanityURL.zoom.us” /> <AttributeRule attributeID=”email”>
<PermitValueRule xsi:type=”basic:ANY”/> </AttributeRule>
<AttributeRule attributeID=”givenName”> <PermitValueRule xsi:type=”basic:ANY”/></AttributeRule>
<AttributeRule attributeID=”surname”>
<PermitValueRule xsi:type=”basic:ANY”/> </AttributeRule>
</AttributeFilterPolicy>
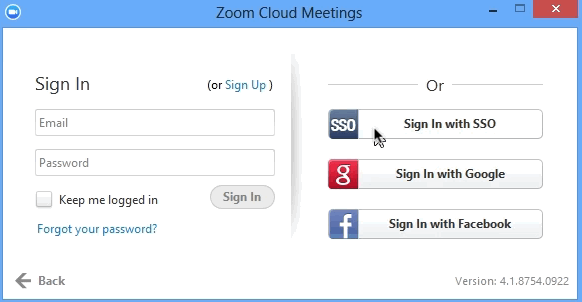
Testing your Configuration
SSO can be tested by logging into the Zoom client and selecting SSO under your Vanity URL or by logging into your vanity URL on the Zoom site.
Read it also –
| How To Configure Zoom With Rsa Securid Access |
| How To Configure Meeting Connector For Domain Name In Zoom |
Frequently Asked Questions
Where is Zoom configuration?
Using the Zoom desktop client, you can access settings in the Zoom client by signing in to your account on the Zoom desktop client. You can access your profile settings by clicking the picture of your profile.
How do I set up zoom on my computer?
Log on to Zoom’s website by using your computer’s internet browser and navigate to Zoom.us to see the Zoom website.
-
Please scroll down to the bottom of the page and click the “Download” button in the footer of the web page you are viewing. …
-
Under the “Zoom Client for Meetings” section of the Download Center page, click on the “Download” link. …
-
You will then be able to download the Zoom app from the Google Play store.
How do I set up and set up a zoom meeting?
Home tab
-
Open Zoom’s desktop client and sign in with your Zoom account.
-
The Home tab will appear once you click it.
-
The down arrow can be clicked (optional) if you wish. You can start your instant meeting by selecting the following option: Start with video: When you choose the Start with video option, your video will be enabled. …
-
You will be able to create a new meeting by clicking New Meeting. If you would like to start an instant meeting, click here.
Why Bluetooth not working with Zoom?
When you join a call and you can’t hear anyone, check if you are not connected to another Bluetooth headset somewhere else in the house if you join a call and you are unable to hear anyone. A possible reason for this could be that your audio has been claimed by another connection already established. You can also use a Bluetooth headset if you wish, but make sure it is connected to the device running Zoom properly, and then use it.
Where is the Zoom sharing key?
When you are using Zoom Rooms, you can share content by tapping on the Share Content button. If you are using a laptop or mobile device, simply open a web browser and visit the link share.zoom.us from your web browser. You will be asked to enter the meeting ID or personal link, and then you will be asked to share the screen. It is also possible for you to enter a sharing key by clicking Enter a Sharing Key.
How do I turn on Zoom sharing?
Then click on Settings. Go to the Meetings tab and click on it. You can enable or disable screen sharing under the In Meeting (Basic) tab by clicking the corresponding toggle switch.
Related Articles
